Hi there!
Thank you for installing File Checksum Generator and trying it out. Here you will find more information and help for File Checksum Generator. As you might have noticed, File Checksum Generator is an extremely easy to use program. It allows you to create cryptographic hash values and checksums for your data and program files to make sure that they have not been modified in any way. It offers you the industry standard hash algorithms MD5, SHA1 and CRC32. Also it makes batch processing and exporting the calculated hash values very easy. Before we start you might want to check out the File Checksum Generator 10 seconds tutorial. Maybe that will already be enough to get you started. Otherwise, let’s get rolling… File Checksum Generator helps you to generate cryptographic hashes for any number of files on your computer.How does it work?
It is extremely simple. After downloading and installing File Checksum Generator you will find an icon of File Checksum Generator on your desktop. It looks like this:
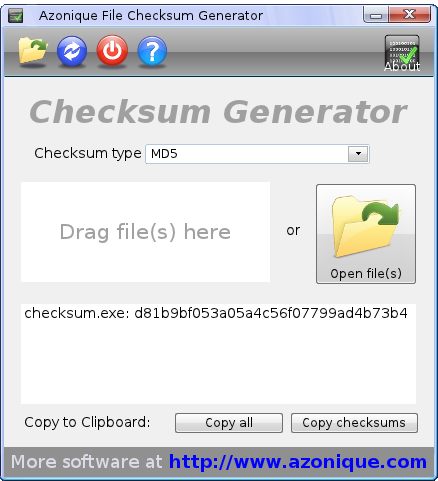
- Open files: Open one or several files to calculate the cryptographic hashes.
- Recalculate: Recalculate the checksums and cryptographic hashes of the files you have already entered. This can be with the same algorithm or you can choose a different algorithm. This can be very handy if you need different hash values of your data since you do not have to reselect all the files.
- Close: closes File Checksum Generator.
- Help: goes to the help page for more information how to use File Checksum Generator.
- About: Show the ‘About’ dialog of File Checksum Generator and some program information
- Checksum type: Choose which cryptographic hash algorithm you want to use. File Checksum Generator offers you MD5, SHA1 and CRC32.
- Drag and Drop field: Drag any number of files from Explorer or another capable file manager into this field and File Checksum Generator starts immediately to calculate the checksums and cryptographic hashes of the dropped files.
- Open file(s): Alternatively you can use this button to get to the file choosing dialog where you can select one or more files. Again, once you have selected the files, File Checksum Generator will immediately start to calculate the cryptographic hashes.
- Output field: The results of the cryptograhic hash calculations will displayed here for your convenience.
- Button “Copy all”: This button copies the full content of the output field to the clipboard.
- Button “Copy checksums”: This button will copy only the cryptographic hash value(s) without the file name(s) to the clipboard. This is particularly useful if you want to use e.g. Excel for further analysis since you will get all the hash values as a handy column which you can easily paste.
- Select the hash algorithm.
- Drag and drop any number of files into the designated field. (Alternatively use the file choose dialog).
- Export the calculated cryptographic hash values.
